Cybersecurity: Best practices in vulnerability management
- 10 April 2024

When it comes to cybersecurity, one crucial aspect is maintaining a coordinated approach between IT and broadcast engineering teams, but this can be a challenge. The absence of synchronized efforts can result in overlooked vulnerabilities, increasing the risk of cyber attacks. In this context, establishing a structured vulnerability management process becomes imperative to ensure effective communication between a customer’s Infosec department, broadcast engineering teams, and suppliers. By following best practices, all stakeholders can be sure that the right measures are taken at the right time, minimizing disruptions to operations.
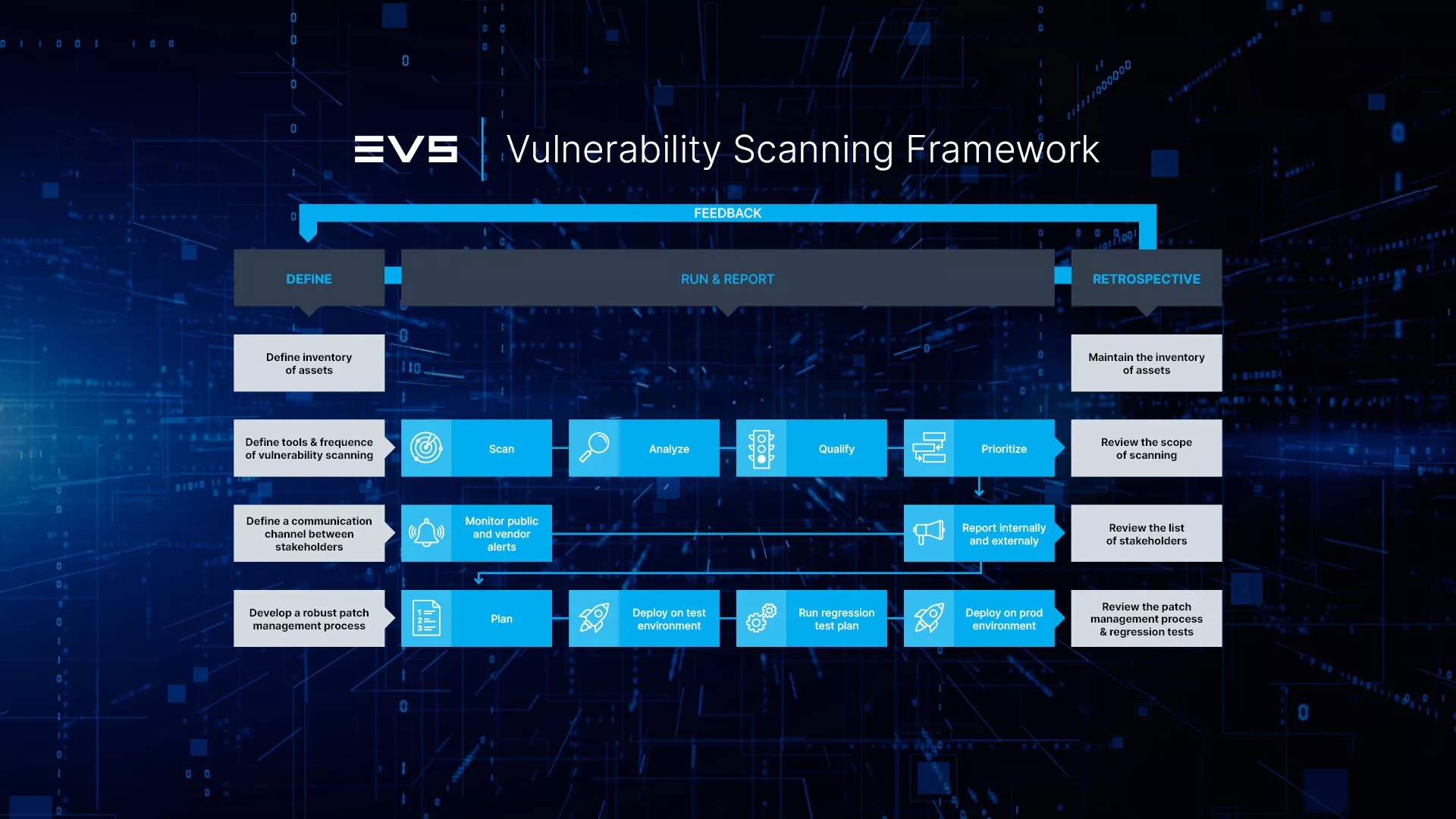
An effective vulnerability management process encompasses several key steps:
- Define inventory of assets
The first step involves establishing a comprehensive inventory of all assets within your broadcast infrastructure, including servers, workstations, network devices, and any other equipment. There is no need for complex tools: sometimes, a simple Excel table is more than enough. The secret is to maintain it.
- Define the tools and the frequency of vulnerability scanning
Establishing a regular schedule for vulnerability scanning is crucial to pinpoint potential security vulnerabilities. Tools like Nessus, Qualys, or OpenVAS (Greenbone) facilitate this process. It's advisable to schedule scans at least monthly or following significant infrastructure alterations. Customers in the broadcast sector should not wait for the results of one vulnerability scan or the resolution of vulnerabilities before initiating another scan. Instead, they require a proactive and continuous approach to vulnerability management, achieved through the implementation of scheduled or automated scanning processes.
- Ensure a communication channel between stakeholders
Effective vulnerability management relies on collaboration between cybersecurity teams, broadcast engineers, and vendors. Ensuring the involvement and alignment of all stakeholders in remediation efforts is paramount. How do you achieve this? Maintain open communication channels with vendors to stay informed about security updates and patches. Subscribe to vendor mailing lists, follow security advisories, and participate in forums or user groups to stay abreast of the latest developments.
- Qualify the risks related to vulnerabilities
Upon completing the scan, it's crucial to analyze the results to identify vulnerabilities, prioritize them based on severity, and evaluate their potential impact on broadcast operations. It's worth noting that scanners may flag vulnerabilities with high scores, but contextual information might reveal that the actual risk is minimal. The Common Vulnerability Scoring System (CVSS) provides a helpful framework for assessing the risk level of each vulnerability. The Base metrics produce a score ranging from 0 to 10, which can then be modified by scoring the Temporal and Environmental metrics. Thus, CVSS is well-suited as a standard measurement system for industries, organizations, and governments that need accurate and consistent vulnerability severity scores. The National Vulnerability Database (NVD) provides CVSS assessments for all published CVE records.
In instances where vulnerabilities are qualified as low-risk, the security team may opt to exclude them from future reports to improve efficiency. It is however important to regularly review the full list to ensure comprehensive coverage.
- Report vulnerabilities to the vendor when applicable
When a vulnerability surfaces within a system provided by the vendor, broadcast engineers can discern whether the issue stems from the environment (e.g., OS) or the vendor's software. If the problem is attributed to the vendor's software and is not documented in the vendor's security bulletin, a support ticket must be raised with the vendor.
- Execute patch implementation
Develop a robust patch management process to swiftly address identified vulnerabilities. This includes establishing a test environment to evaluate patches before their deployment in the production environment. It is strongly recommended to check advisories published by vendors, such as security bulletins from EVS.
- Maintain the inventory of assets
The definition of the inventory of assets is the first step. But we all know that a broadcast infrastructure is a “living environment”. It is essential that the broadcast engineers are made conscious of the need to declare in and out infrastructure elements as a process. It is also a good practice to run the automated tools at regular interval to detect inconsistencies.
At EVS, we have internal processes to detect vulnerabilities by scanning our products before delivering them to our customers. We also specifically tag support tickets related to vulnerabilities in our products so that we can prioritize them according to the level of risk.
Sometimes, these vulnerabilities arise due to an outdated environment (e.g. OS). In that case, it is up to the customer to apply OS patching. EVS provides guidance related to the most frequent environment where EVS products are operated. Click here to view our security bulletins.
When a vulnerability is related to the EVS application, R&D is added in the process to fix it in the next release or with a specific security patch. EVS finally also hired cybersecurity experts to help our customers with this complex matter.
Remember, security is a journey, not a destination—continuously assess, adapt, and improve your security posture to stay ahead of threats. Proactive vulnerability management as a process is essential for safeguarding broadcast infrastructure against evolving cyber threats.

Find out how EVS can help you safeguard your network and your assets.

For more information on the topic, download our whitepaper ‘5 steps to make live production workflows cyber-secure’.